Maximize the security of your business by keeping your data safe
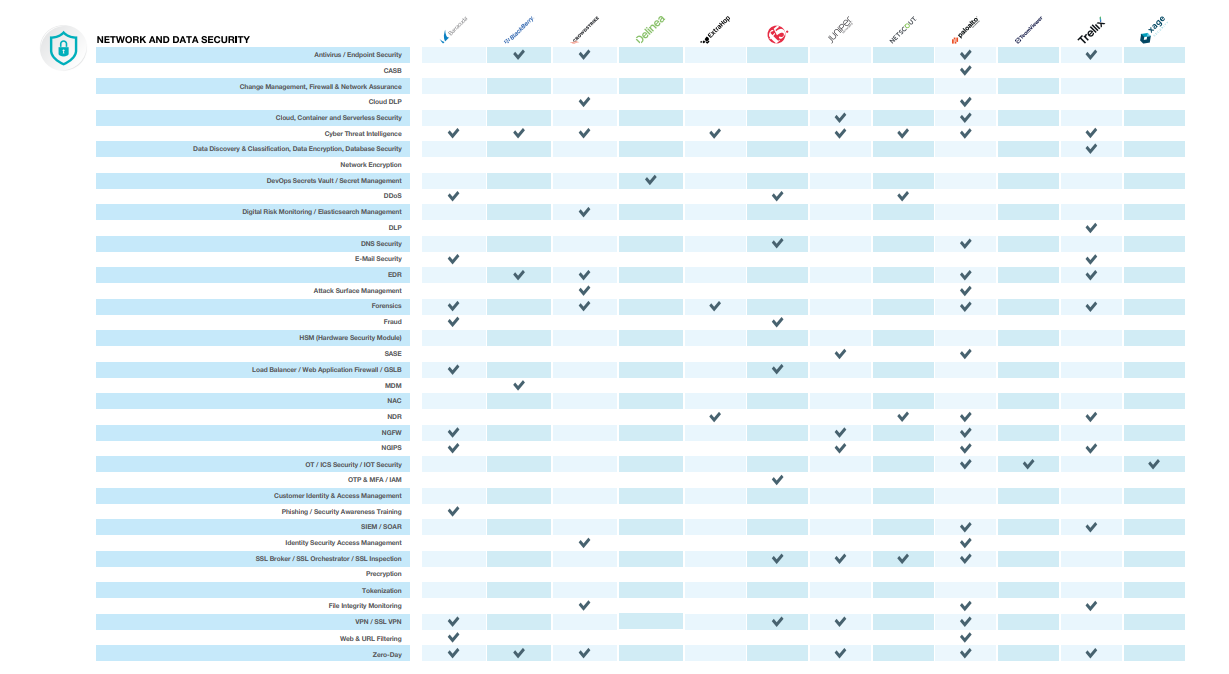
It is important for companies to ensure data security as a whole. Ensuring data security, which is extremely important for both companies and users, can be provided effectively with policies to be created in different security devices or software. To ensure the security of the company, visibility and end-to-end controls must be ensured from the outermost layer to the innermost layer of the corporate network.
It is very important to ensure the security of encryption transactions on platforms where online payments are made, such as e-commerce sites. In systems that effectively protect other sensitive data such as users' identification numbers, many different equipment such as EFT transactions and document signing are maintained in a healthy way. Necessary cyber security measures are taken to protect sensitive information such as credit cards in systems that offer satisfactory options in terms of security and performance. In accordance with the PCI DSS standard, which is necessary to ensure the security of credit card information, and the security measures that the organization will choose to protect its customers or business partners, it will analyze your system and guide you to take appropriate measures.
Preventing data access, which is one of the methods applied to ensure data security, is ideal for people who you want to have access to data specifically or for whom you want to block access to data. Enriched with special software that allows data to be protected even if it is in the hands of unauthorized persons, and supported by new generation technologies, applications ensure full protection of data.
Data classification, which is another step in ensuring data security, is based on the principle of categorizing data that are likely to exist in different environments. After the classified data are determined according to their criticality, necessary measures are taken to protect the data. It is very important to classify the data according to the degree of criticality for the efficient implementation of corporate policies. After the classification process, the precautions to be taken and the steps to be taken can be determined.
In order to prevent data leakage in devices used in the company or used individually, sensitive data within the institution should be prevented from leaving the institution by means of flash memories, e-mails, uploading files to the cloud, instant messaging, etc. With different analyzes, methods developed to protect data can work in integration with different applications with content filtering features.
Network security usually starts with authentication using a username and password. However, north-south and east-west traffic needs to be controlled in several different layers. Many different attack methods developed reveal this necessity. For a strong security, your security device or software needs to be able to recognize applications, analyze these applications, prevent attacks to consume bandwidth, protect against known attacks and zero-day attacks, and prevent users from accessing harmful sites with content filtering.
It is important for companies to ensure data security as a whole. Ensuring data security, which is extremely important for both companies and users, can be provided effectively with policies to be created in different security devices or software. To ensure the security of the company, visibility and end-to-end controls must be ensured from the outermost layer to the innermost layer of the corporate network. Controls should start with the provision of controlled access to company resources at the outermost layer, and in this context, they should contribute to the effective use of resources, and finally, they should be able to prevent the company's valuable data from being stolen or unauthorized users from using this data. While doing this, one of the most important points is that hardware or software used for security purposes can share information in integration with each other and take action accordingly.